Cyber made practical. Learn, practice, and apply—faster
than scrolling another forum thread.
Train. Defend. Conquer.
Top 10 Cyber Hygiene Habits
Top 10 Cyber Hygiene Habits Every Beginner Must Master
Because Digital Strength Begins with Discipline
“The greatest battles are won before they are fought.” — Sun Tzu, The Art of War
In cyberspace, every click is a choice, every password a shield, every update a weapon.
We live in an era where the digital self mirrors, and often defines, the real self—from identity to finance, from memory to mission. Yet, for all its power, technology remains fragile, for it inherits the flaws of its user.
Cyber hygiene is not a checklist—it is a mindset of disciplined awareness.
It is to cybersecurity what handwashing is to medicine: preventive, habitual, and lifesaving.
Whether you are a student entering your first lab or a manager navigating corporate firewalls, these ten habits form the foundation of digital resilience.
🥋 1. Guard Your Passwords Like Sacred Keys
A password is more than a credential—it is the boundary between self and system.
Weak passwords remain the most exploited vulnerability in global cyber incidents.
Habit to Master:
Create unique, complex, and lengthy passwords for every account (at least 12 characters with a mix of letters, numbers, and symbols). Use a reputable password manager to generate and store them securely.
Why It Matters:
The mind resists remembering many combinations, so humans reuse passwords—a predictable habit that attackers exploit. Each reused password is a domino waiting to fall.
Upgrade the Mindset:
Treat your passwords as digital DNA—never replicated, always protected. When convenience tempts reuse, remember: ease is the enemy of security.
🔐 2. Enable Multi-Factor Authentication (MFA)
If passwords are walls, MFA is the gatekeeper that verifies who you are.
It demands an additional proof—something you have (a token or phone), are (fingerprint, face), or do (behavioral pattern).
Habit to Master:
Enable MFA on email, banking, cloud storage, and social accounts. Avoid SMS codes where possible; use authenticator apps or hardware keys instead.
Why It Matters:
Studies show MFA blocks over 99 percent of automated attacks. Yet many ignore it because it adds seconds of friction. Those seconds can save months of recovery.
Upgrade the Mindset:
Security is not about removing friction; it’s about building intentional resistance—a small barrier that deters colossal harm.
🧩 3. Update Relentlessly — Patch Before You’re Breached
Outdated software is a silent trapdoor. Each patch or update is a repair to an exposed nerve in the system’s body.
Habit to Master:
Turn on automatic updates for operating systems, browsers, and applications. Regularly check firmware updates for routers and IoT devices.
Why It Matters:
Over 60 percent of breaches occur because known vulnerabilities were left unpatched. Cyber attackers scan the internet for unpatched devices—the digital equivalent of unlocked doors.
Upgrade the Mindset:
An update is not a nuisance; it is an immunization. Every patch day is a training day for your digital immune system.
🧭 4. Beware of Phishing — The Art of Digital Deception
Phishing remains the psychological theater of cybercrime—a fusion of persuasion and illusion.
Attackers no longer exploit code; they exploit confidence, curiosity, and fear.
Habit to Master:
Hover over links before clicking, verify sender addresses, and distrust urgency. Never provide credentials through email or text.
Why It Matters:
Over 90 percent of successful breaches begin with a phishing email. The target is not your inbox—it is your impulse.
Upgrade the Mindset:
Every message is a test of awareness.
Pause before you click. That pause is the difference between control and compromise.
💾 5. Back Up, Then Back Up Again
Data is the bloodstream of digital life. To lose it is to lose identity, memory, and trust.
Backup is not about paranoia—it is about continuity of consciousness.
Habit to Master:
Maintain two backups: one on a cloud service and another on a disconnected external drive. Automate your backup schedule and verify it monthly.
Why It Matters:
Ransomware thrives on victims who fail to back up. When data is hostage, the one with a backup remains free.
Upgrade the Mindset:
Think of backups as time machines—each copy a version of your digital past preserved against the chaos of the present.
🧱 6. Secure Your Network Fortress
Your Wi-Fi is the front gate of your digital castle. A weak password, outdated router, or exposed IoT device can invite unseen intruders.
Habit to Master:
Change default router credentials, use WPA3 encryption, and regularly reboot your router to clear malicious code. Segment smart devices from personal systems on a separate network.
Why It Matters:
Many home routers remain unpatched for years. Cybercriminals use them as launch pads for wider attacks, sometimes turning your home into a zombie hub.
Upgrade the Mindset:
A fortress is only as strong as its forgotten gate.
Audit your network monthly—the discipline of the unseen is the hallmark of the Cyber Ninja.
🔍 7. Master the Art of Privacy
In a surveillance economy, privacy is resistance.
Each shared photo, tagged location, or online quiz reveals fragments of identity that form exploitable patterns.
Habit to Master:
Review privacy settings on social media, browsers, and apps. Disable location tracking where unnecessary, and use privacy-focused search engines and browsers (DuckDuckGo, Brave, or Firefox with enhancements).
Why It Matters:
Data is the new gold—and you are the mine. The more data extracted, the more predictable and manipulable you become.
Upgrade the Mindset:
Privacy is not secrecy; it is self-respect. To protect your data is to reclaim your autonomy.
🧠 8. Think Before You Share — Social Engineering Resistance
Attackers rarely need to hack databases when they can hack people.
Social engineering exploits trust, kindness, and overconfidence—the most human of vulnerabilities.
Habit to Master:
Before revealing personal or professional information, verify identity through a secondary channel. Avoid oversharing your routines, company details, or security setups online.
Why It Matters:
Information scattered across platforms can be pieced together into a weaponized profile.
Upgrade the Mindset:
Every post is a potential footprint. Walk lightly in the digital forest; even friendly eyes may be predatory.
⚙️ 9. Maintain Device Discipline
The modern warrior wields many weapons—laptop, phone, tablet—but neglect often compromises them.
Each neglected device is a forgotten sword left unsharpened.
Habit to Master:
Use device encryption, strong passcodes, and auto-lock timers. Avoid public Wi-Fi for sensitive transactions or use a trusted VPN. Regularly uninstall unused apps and review permissions.
Why It Matters:
A single lost or stolen device without encryption can lead to catastrophic identity theft. Most mobile breaches originate from careless configurations, not sophisticated hacks.
Upgrade the Mindset:
Treat every device as a soldier: keep it trained, disciplined, and ready. Idle devices attract invisible battles.
🌐 10. Practice Continuous Awareness — The Eternal Vigil
Cybersecurity is not static—it evolves daily, like language or biology. The final and greatest habit is curiosity sustained by humility.
Habit to Master:
Dedicate 15 minutes each week to reading security news, learning about new scams, or revisiting your setup. Follow credible sources (CISA, SANS Internet Storm Center, Krebs on Security).
Why It Matters:
Threats adapt faster than policies. Continuous learning transforms users from passive consumers to active guardians.
Upgrade the Mindset:
In the dojo of cybersecurity, mastery is never final.
Awareness is a lifelong meditation—each login an opportunity to practice it.
⚔️ The Philosophy Behind Cyber Hygiene
Cyber hygiene is not fear-driven—it is discipline-driven.
The myths that “hackers only target big companies” or “antivirus software is enough” are illusions.
Attackers follow psychology, not prestige. The moment you connect, you become a potential node.
Cyber hygiene redefines security from a reactive pursuit to a proactive philosophy.
It teaches three eternal principles:
-
Vigilance is Protection. What you monitor, you control.
-
Consistency is Armor. Small habits practiced daily outweigh emergency responses.
-
Ethics is Purpose. To secure systems is to protect people; to protect people is to preserve trust.
🌱 From User to Guardian — The Way of the Cyber Ninja
The Cyber Ninja’s path begins not with tools, but with habits—simple, repeatable, deliberate.
Cyber hygiene is the dojo where discipline meets awareness, where beginners forge the reflexes that define experts.
Start with one habit. Then another. Let repetition sculpt resilience.
The digital world does not need more users—it needs guardians with integrity, curiosity, and constancy.
“Security is not a product; it is a practice.” — Bruce Schneier
So, practice daily.
And remember:
Every click is a choice. Every choice builds a defender—or a victim.
Be the former. Be the Ninja.
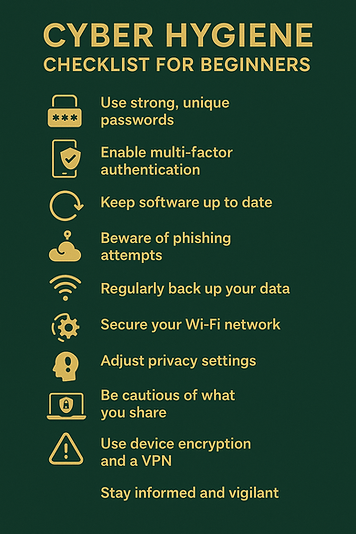
✅ Summary: Top 10 Cyber Hygiene Habits
-
Strong, unique passwords.
-
Multi-factor authentication.
-
Timely updates & patching.
-
Phishing awareness.
-
Regular backups.
-
Secured Wi-Fi network.
-
Privacy management.
-
Social engineering resistance.
-
Device discipline.
-
Continuous learning & awareness.
🔒 Call to Action for GoCyberNinja.net
Train. Defend. Conquer.
Visit the Learn → Core Skills → Cyber Hygiene section to explore interactive tutorials, checklists, and daily security challenges designed to turn habits into mastery.